Dynamic IP and Port NAT
Dynamic IP and port (DIPP) NAT allows you to use each translated IP address and port pair multiple times (eight, four, or two times) in concurrent sessions. This re-usability of an IP address and port (known as oversubscription) provides scalability for customers who have too few public IP addresses. The design is based on the assumption that hosts are connecting to different destinations, therefore sessions can be uniquely identified and collisions are unlikely. The oversubscription rate in effect multiplies the original size of the address/port to eight, four, or two times the size. For example, the default limit of 64K concurrent sessions allowed, when multiplied by an oversubscription rate of eight, results in 512K concurrent sessions allowed.
The oversubscription rates that are allowed vary based on the platform. The oversubscription rate is global; it applies to the firewall. This oversubscription rate is set by default and consumes memory, even if you have enough public IP addresses available to make oversubscription unnecessary. You can reduce the rate from the default setting to a lower setting or to even 1 (which means no oversubscription). By configuring a reduced rate, you decrease the number of source device translation possible, but increase the DIP and DIPP NAT rule capacities.
Details about this capability and its configuration can be found on this link.
Security Policy
The Security policy consists of numerous security rules that are the keystone of the firewall's ability to enable or block sessions. Numerous match conditions can be used when creating these rules. Security zones, source and destination IP address, application (App-ID), source user (User-ID), service (port), HIP match, and URL categories in the case of web traffic all can serve as traffic matching criteria for allow/block decision making. Allowed sessions can be scanned further based on Security profiles (Content-ID) to identify unwanted packet content. These Profiles use known threat signatures and a mechanism (WildFire) to identify unknown threats, automatically generating new threat signatures.
Security policies are used to create a positive (whitelist) and/or negative (blacklist) enforcement model for traffic flowing through the firewall. In order for the firewall to properly evaluate, configure, and maintain Security policies, the necessary rules must be in place. These rules are enumerated from the top down, and the first rules with the appropriate matching conditions will allow or deny the traffic matching. If the logging is enabled on the matching rule, and the traffic crosses a zone, the action for that session is logged. These logs are extremely useful for adjusting the positive/negative enforcement model. The log information can be used to characterize traffic, providing specific usage information and allowing precise policy creation and control. Palo Alto Networks firewall logs, Application Command Center, App Scope, and other reporting tools all work to precisely describe traffic and usage patterns.
Choose Interface Address under Address
Security Policy Rules
You can see all Applications (and create Application objects) that is supported on the PAN firewall by going to Objects > Applications.
You can do a type and search for a specific Application or click under each category. In this example I want to see peer-to-peer Application by clicking on general-internet > file-sharing > peer-to-peer > click bittorrent to see more info.
Click OK and Commit. There's a warning that requires icmp Application to be allowed for traceroute to work. I've tested traceroute to be working even without adding icmp in the ALLOW-PING rule.
I've ended up adding the icmp Application on the ALLOW-PING rule since the warning keeps popping up every time I hit Commit. You can quickly edit a Security rule and add an Application by clicking ALLOW-PING > under Application tab click Add > type and search: icmp > click on icmp > OK > Commit.
This is a Detailed Log View for a ping (it displayed insufficient-data Application) when it hit the ALLOW-PING rule. You can click on the green arrow (pointing downward) to view the Packet Capture.
I've configured SW1 port 22 for User VLAN 101 access and connected a PC with a static IP address of 172.17.101.3/24.
SW1#show run interface fastethernet0/22
Building configuration...
Current configuration : 110 bytes
!
interface FastEthernet0/22
switchport access vlan 101
switchport mode access
spanning-tree portfast
end
C:\Users\John Lloyd>ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::4562:9b92:c15f:91ff%10
IPv4 Address. . . . . . . . . . . : 172.17.101.3
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.17.101.1
C:\Users\John Lloyd>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8: bytes=32 time=8ms TTL=53
Reply from 8.8.8.8: bytes=32 time=11ms TTL=53
Reply from 8.8.8.8: bytes=32 time=8ms TTL=53
Reply from 8.8.8.8: bytes=32 time=9ms TTL=53
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 8ms, Maximum = 11ms, Average = 9ms
C:\Users\John Lloyd>tracert 8.8.8.8
Tracing route to google-public-dns-a.google.com [8.8.8.8]
over a maximum of 30 hops:
1 2 ms 1 ms 1 ms 172.17.101.1
2 <1 ms <1 ms <1 ms 172.17.99.1
3 11 ms 9 ms 8 ms 10.47.0.1
4 6 ms 7 ms 8 ms 172.20.43.65
5 13 ms 7 ms 7 ms 172.20.9.226
6 11 ms 9 ms 7 ms 203.116.188.85
7 9 ms 7 ms 7 ms 203.117.36.21
8 8 ms 8 ms 7 ms 203.116.189.181
9 20 ms 6 ms 7 ms 203.117.34.34
10 6 ms 6 ms 7 ms 72.14.196.189
11 8 ms 7 ms 7 ms 108.170.242.65
12 9 ms 7 ms 7 ms 64.233.175.213
13 10 ms 7 ms 7 ms google-public-dns-a.google.com [8.8.8.8]
Trace complete.
Below are some useful CLI commands on the PA-200 firewall.
admin@PA-200-LAB> show running nat-policy
SOURCE-NAT-TRUST {
from TRUST-L3;
source 172.17.101.0/24;
to UNTRUST-L3;
to-interface ethernet1/1 ;
destination any;
service any/any/any;
translate-to "src: ethernet1/1 222.165.123.45(*) (dynamic-ip-and-port) (
pool idx: 1)";
terminal no;
}
admin@PA-200-LAB> show running ippool
Total active sessions: 14
Rule Used Available
-------------------------------- ---------- ----------
SOURCE-NAT-TRUST 5 129019
admin@PA-200-LAB> show session
> all Show active sessions
> id Show specific session information
> info Show session statistics
> meter Show session metering statistics
> rematch Show rematch statistics
admin@PA-200-LAB> show session all
+ filter Apply show session filter
+ start-at Show next 1K sessions
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> show session all // SIMILAR TO CISCO ASA show xlate COMMAND
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated
IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Por
t])
--------------------------------------------------------------------------------
838 ssl ACTIVE FLOW NS 172.17.101.3[4325]/TRUST-L3/6 (222.165.112.234[21607])
vsys1 96.6.67.248[443]/UNTRUST-L3 (96.6.67.248[443])
1126 undecided DISCARD FLOW 216.218.206.72[50132]/UNTRUST-L3/
6 (216.218.206.72[50132])
vsys1 222.165.112.127[7547]/UNTRUST-L3
(222.165.112.234[7547])
1127 undecided DISCARD FLOW 189.155.182.200[7547]/UNTRUST-L3/
6 (189.155.182.200[7547])
vsys1 222.165.112.234[23]/UNTRUST-L3 (
222.165.112.234[23])
1125 undecided DISCARD FLOW 139.162.91.116[45073]/UNTRUST-L3/
6 (139.162.91.116[45073])
vsys1 222.165.112.234[443]/UNTRUST-L3
(222.165.112.234[443])
1000 web-browsing ACTIVE FLOW NS 172.17.101.3[4395]/TRUST-L3/6 (222.165.112.234[1739])
vsys1 77.234.41.24[80]/UNTRUST-L3 (77.
234.41.24[80])
816 ssl ACTIVE FLOW NS 172.17.101.3[4320]/TRUST-L3/6 (222.165.112.234[47596])
vsys1 124.155.222.163[443]/UNTRUST-L3
(124.155.222.163[443])
696 ssl ACTIVE FLOW NS 172.17.101.3[4283]/TRUST-L3/6 (2
22.165.112.127[10265])
vsys1 104.27.192.92[443]/UNTRUST-L3 (104.27.192.92[443])
800 ssl ACTIVE FLOW NS 172.17.101.3[4315]/TRUST-L3/6 (222.165.112.234[1370])
vsys1 23.50.87.174[443]/UNTRUST-L3 (23.50.87.174[443])
824 ocsp ACTIVE FLOW NS 172.17.101.3[4322]/TRUST-L3/6 (222.165.112.234[6458])
vsys1 23.50.91.27[80]/UNTRUST-L3 (23.5
0.91.27[80])
766 ssl ACTIVE FLOW NS 172.17.101.3[4306]/TRUST-L3/6 (2
22.165.112.127[15483])
vsys1 74.125.200.104[443]/UNTRUST-L3 (74.125.200.104[443])
1128 undecided DISCARD FLOW 134.196.15.164[25680]/UNTRUST-L3/
6 (134.196.15.164[25680])
vsys1 222.165.112.234[5358]/UNTRUST-L3
(222.165.112.234[5358])
856 ssl ACTIVE FLOW NS 172.17.101.3[4335]/TRUST-L3/6 (222.165.112.234[62636])
vsys1 23.50.85.25[443]/UNTRUST-L3 (23.
50.85.25[443])
700 google-talk-base ACTIVE FLOW NS 172.17.101.3[4287]/TRUST-L3/6
(222.165.112.234[26535])
vsys1 74.125.68.188[443]/UNTRUST-L3 (74.125.68.188[443])
177 ssl ACTIVE FLOW NS 172.17.101.3[3549]/TRUST-L3/6 (2
22.165.112.127[19868])
vsys1 172.217.24.98[443]/UNTRUST-L3 (172.217.24.98[443])
912 ssl ACTIVE FLOW NS 172.17.101.3[4356]/TRUST-L3/6 (2
22.165.112.127[20406])
vsys1 23.10.16.154[443]/UNTRUST-L3 (23.10.16.154[443])
You can test NAT policy, Security rule and PBF policy using the test command (similar to Cisco ASA firewall packet-tracer command).
admin@PA-200-LAB> test
> arp ARP related
> botnet Test botnet domain categorization
> cp-policy-match Test cp policy match
> custom-url Test custom URL categorization
> data-filtering Test ccn/ssn match
> decryption-policy-match Test ssl policy match
> dns-proxy Test DNS query
> dos-policy-match Test DoS Policy match
> global-protect-mdm Test MDM
> global-protect-satellite Test GlobalProtect satellite
> nat-policy-match Test nat policy match
> nd IPv6 Neighbor Discovery
> pbf-policy-match Test Policy Based forwarding match
> pppoe test pppoe connection
> qos-policy-match Test qos policy match
> routing verify routing settings
> scp-server-connection Test scp server connection
> security-policy-match Test security policy match
> stats-service Test statistics service
> tag-filter Test a tag-based filter
> url Test URL categorization
> url-info-cloud Return detailed information about the URL in the cloud
--more--
> url-info-host Return detailed information about the URL in the MP
> user-id Test Userid
> vpn verify (IKE/IPSec) VPN settings
> wildfire Test wildfire
admin@PA-200-LAB> test security-policy-match
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ from from
+ protocol IP protocol value
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol
<value> <1-255> IP protocol value
admin@PA-200-LAB> test security-policy-match protocol 1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ from from
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from
TRUST-L3 TRUST-L3
UNTRUST-L3 UNTRUST-L3
any Any
trust trust
untrust untrust
<value> From zone
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to
TRUST-L3 TRUST-L3
UNTRUST-L3 UNTRUST-L3
any Any
multicast Multicast
trust trust
untrust untrust
<value> To zone
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source
<ip> <ip>
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination
<ip/netmask> <ip/netmask>
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
+ application Application name
+ category Category name
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8 destination-port
+ application Application name
+ category Category name
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
<value> <1-65535> Destination port
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
ALLOW-PING {
from TRUST-L3;
source 172.17.101.0/24;
source-region none;
to UNTRUST-L3;
destination any;
destination-region none;
user any;
category any;
application/service [ ping/any/any/any traceroute/any/any/any ];
action allow;
terminal yes;
}
admin@PA-200-LAB> configure
Entering configuration mode
[edit]
admin@PA-200-LAB# save
> config config
> device-state Save files needed to restore device
admin@PA-200-LAB# save config
+ to Filename
<Enter> Finish input
admin@PA-200-LAB# save config
Config saved to .snapshot.xml
Dynamic IP and port (DIPP) NAT allows you to use each translated IP address and port pair multiple times (eight, four, or two times) in concurrent sessions. This re-usability of an IP address and port (known as oversubscription) provides scalability for customers who have too few public IP addresses. The design is based on the assumption that hosts are connecting to different destinations, therefore sessions can be uniquely identified and collisions are unlikely. The oversubscription rate in effect multiplies the original size of the address/port to eight, four, or two times the size. For example, the default limit of 64K concurrent sessions allowed, when multiplied by an oversubscription rate of eight, results in 512K concurrent sessions allowed.
The oversubscription rates that are allowed vary based on the platform. The oversubscription rate is global; it applies to the firewall. This oversubscription rate is set by default and consumes memory, even if you have enough public IP addresses available to make oversubscription unnecessary. You can reduce the rate from the default setting to a lower setting or to even 1 (which means no oversubscription). By configuring a reduced rate, you decrease the number of source device translation possible, but increase the DIP and DIPP NAT rule capacities.
Details about this capability and its configuration can be found on this link.
Security Policy
The Security policy consists of numerous security rules that are the keystone of the firewall's ability to enable or block sessions. Numerous match conditions can be used when creating these rules. Security zones, source and destination IP address, application (App-ID), source user (User-ID), service (port), HIP match, and URL categories in the case of web traffic all can serve as traffic matching criteria for allow/block decision making. Allowed sessions can be scanned further based on Security profiles (Content-ID) to identify unwanted packet content. These Profiles use known threat signatures and a mechanism (WildFire) to identify unknown threats, automatically generating new threat signatures.
Security policies are used to create a positive (whitelist) and/or negative (blacklist) enforcement model for traffic flowing through the firewall. In order for the firewall to properly evaluate, configure, and maintain Security policies, the necessary rules must be in place. These rules are enumerated from the top down, and the first rules with the appropriate matching conditions will allow or deny the traffic matching. If the logging is enabled on the matching rule, and the traffic crosses a zone, the action for that session is logged. These logs are extremely useful for adjusting the positive/negative enforcement model. The log information can be used to characterize traffic, providing specific usage information and allowing precise policy creation and control. Palo Alto Networks firewall logs, Application Command Center, App Scope, and other reporting tools all work to precisely describe traffic and usage patterns.
You'll need to configure Source NAT (also known as PAT or NAT
overload) to allow multiple internal devices (on TRUST Zone) to reach the
UNTRUST Zone or the Internet. Create first an object for the TRUST Zone users by
going to Objects >Addresses > Add.
Type the name of the
Address object (TRUST-ZONE-USERS in this case), optionally add a Description,
choose IP Netmask under Type > type the IP address/netmask > click OK.
Next, configure the NAT policy by going to Policies > NAT > Add.
You configure a NAT policy starting from left tab going to right. Under General tab > type the name of
the NAT policy (SOURCE-NAT-TRUST) and optionally add a description > leave NAT Type as IPv4.
Under Original Packet tab, also configure from left to
right > Source Zone > Add > choose TRUST-L3.
Under Destination Zone
> choose UNTRUST-L3 > under Destination Interface choose ethernet1/1.
Leave the default of Any
for Service (TCP, UDP, etc) and Destination Address. Choose TRUST-ZONE-USERS under Source Address.
Under Translated
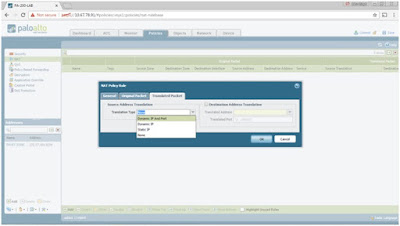
Packet > Translation Type > choose Dynamic IP and Port.
Choose Interface Address under Address
Choose ethernet1/1
under Interface.
The IP Address field is grayed out since ethernet1/1
is a DHCP Client and gets an automatic public IP address assignment from the ISP (via the cable modem).
Security Policy Rules
By default, a PAN firewall doesn't allow traffic from
one Security zone to another without a Security rule allowing it. To allow TRUST zone users to reach the UNTRUST zone or the Internet, you'll need to create a Security rule by going to Policies > Security.
There is a default Security policy named rule1, which allows all traffic (any port, service or application)
from the trust zone to untrust zone. You can either delete rule1 or modify it. I've deleted rule1 and created a new
custom rule.
Before creating a new rule, you need create a service object (like an
alias) by going to Objects > Services.
There are two default service objects: HTTP (service-http) and HTTPS (service-https).
Create a new service object for DNS (service-dns in this case) by clicking Add > type the name
service-dns (to have a consistent name) > click UDP > type 53 on
Destination Port field > click OK.
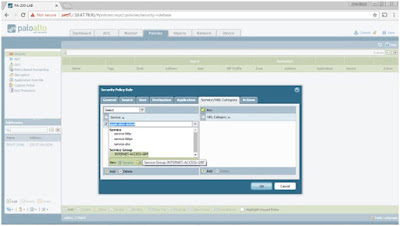
You can also combine service objects to have a "clean" Security rule (less rule entries) by going to Objects
> Service Groups > Add > type the name of the Service Group (INTERNET-ACCESS-GROUP in this case) > click
Add under Service > choose HTTP, HTTPS and DNS services > click OK.
Go back to Policies
> Security > click the default rule1 (click the number 1 on the first column) >
Delete.
Create a new Security rule by clicking Add. You configure the
Security rule from left to right just like the NAT policy.
Under General tab,
type the name of the Security rule (USER-INTERNET-ACCESS in this case) >
optionally add a Description.
Under Source tab >
click Add under Source Zone and choose TRUST-L3 > choose TRUST-ZONE-USERS
(which is subnet 172.17.101.0/24) under Source Address.
Under Destination tab
> add UNTRUST-L3 under Destination Zone > leave Any under Destination
Address (which is any Internet Address).
Under Service/URL
Category tab > choose the Service Object group created earlier (INTERNET-ACCESS-GRP) instead of
individual services > leave the default of Any under URL Category.
Under Actions >
leave the default Action Setting of Allow and Log Setting of Log at Session End
> click OK > click Commit.
My PC was able to go the Internet and typed whatsmyip on the web browser to show ethernet1/1 (DHCP) public
IP address assigned by the ISP. However, I couldn’t ping and traceroute to Google's public DNS 8.8.8.8.
The PAN firewall can also inspect Application headers and payload aside from just filtering traditional TCP and UDP ports. I was able to ping and do a traceroute by adding another Security rule (ALLOW-PING) which allows the ping and traceroute Application. I tried adding icmp, ping and traceroute on USER-INTERNET-ACCESS rule (under the Applications tab) but web browsing, ping and traceroute didn't work.
The PAN firewall can also inspect Application headers and payload aside from just filtering traditional TCP and UDP ports. I was able to ping and do a traceroute by adding another Security rule (ALLOW-PING) which allows the ping and traceroute Application. I tried adding icmp, ping and traceroute on USER-INTERNET-ACCESS rule (under the Applications tab) but web browsing, ping and traceroute didn't work.
You can see all Applications (and create Application objects) that is supported on the PAN firewall by going to Objects > Applications.
You can do a type and search for a specific Application or click under each category. In this example I want to see peer-to-peer Application by clicking on general-internet > file-sharing > peer-to-peer > click bittorrent to see more info.
To create an Application rule, click on rule 1
(USER-INTERNET-ACCESS) > Clone (to copy rule 1) > rename the rule (ALLOW-PING in this case).
Under Application tab > type and search: ping (click on ping) > type and search: traceroute (click on traceroute).
Under Service/URL Category > click INTERNET-ACCESS-GRP
> Delete > choose any from the drop-down option (above Service).
I've ended up adding the icmp Application on the ALLOW-PING rule since the warning keeps popping up every time I hit Commit. You can quickly edit a Security rule and add an Application by clicking ALLOW-PING > under Application tab click Add > type and search: icmp > click on icmp > OK > Commit.
To confirm NAT, Internet and ping are working on the PAN firewall, go to
Monitor > Traffic. Notice end under the Type column which means the syslog has ended
for the specific session.
Click the magnifying glass on a specific session to see its Detailed Log View. This is a Detailed Log View for a DNS traffic that hit the USER-INTERNET-ACCESS rule.
I've configured SW1 port 22 for User VLAN 101 access and connected a PC with a static IP address of 172.17.101.3/24.
SW1#show run interface fastethernet0/22
Building configuration...
Current configuration : 110 bytes
!
interface FastEthernet0/22
switchport access vlan 101
switchport mode access
spanning-tree portfast
end
C:\Users\John Lloyd>ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::4562:9b92:c15f:91ff%10
IPv4 Address. . . . . . . . . . . : 172.17.101.3
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.17.101.1
C:\Users\John Lloyd>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8: bytes=32 time=8ms TTL=53
Reply from 8.8.8.8: bytes=32 time=11ms TTL=53
Reply from 8.8.8.8: bytes=32 time=8ms TTL=53
Reply from 8.8.8.8: bytes=32 time=9ms TTL=53
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 8ms, Maximum = 11ms, Average = 9ms
C:\Users\John Lloyd>tracert 8.8.8.8
Tracing route to google-public-dns-a.google.com [8.8.8.8]
over a maximum of 30 hops:
1 2 ms 1 ms 1 ms 172.17.101.1
2 <1 ms <1 ms <1 ms 172.17.99.1
3 11 ms 9 ms 8 ms 10.47.0.1
4 6 ms 7 ms 8 ms 172.20.43.65
5 13 ms 7 ms 7 ms 172.20.9.226
6 11 ms 9 ms 7 ms 203.116.188.85
7 9 ms 7 ms 7 ms 203.117.36.21
8 8 ms 8 ms 7 ms 203.116.189.181
9 20 ms 6 ms 7 ms 203.117.34.34
10 6 ms 6 ms 7 ms 72.14.196.189
11 8 ms 7 ms 7 ms 108.170.242.65
12 9 ms 7 ms 7 ms 64.233.175.213
13 10 ms 7 ms 7 ms google-public-dns-a.google.com [8.8.8.8]
Trace complete.
Below are some useful CLI commands on the PA-200 firewall.
admin@PA-200-LAB> show running nat-policy
SOURCE-NAT-TRUST {
from TRUST-L3;
source 172.17.101.0/24;
to UNTRUST-L3;
to-interface ethernet1/1 ;
destination any;
service any/any/any;
translate-to "src: ethernet1/1 222.165.123.45(*) (dynamic-ip-and-port) (
pool idx: 1)";
terminal no;
}
admin@PA-200-LAB> show running ippool
Total active sessions: 14
Rule Used Available
-------------------------------- ---------- ----------
SOURCE-NAT-TRUST 5 129019
admin@PA-200-LAB> show session
> all Show active sessions
> id Show specific session information
> info Show session statistics
> meter Show session metering statistics
> rematch Show rematch statistics
admin@PA-200-LAB> show session all
+ filter Apply show session filter
+ start-at Show next 1K sessions
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> show session all // SIMILAR TO CISCO ASA show xlate COMMAND
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated
IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Por
t])
--------------------------------------------------------------------------------
838 ssl ACTIVE FLOW NS 172.17.101.3[4325]/TRUST-L3/6 (222.165.112.234[21607])
vsys1 96.6.67.248[443]/UNTRUST-L3 (96.6.67.248[443])
1126 undecided DISCARD FLOW 216.218.206.72[50132]/UNTRUST-L3/
6 (216.218.206.72[50132])
vsys1 222.165.112.127[7547]/UNTRUST-L3
(222.165.112.234[7547])
1127 undecided DISCARD FLOW 189.155.182.200[7547]/UNTRUST-L3/
6 (189.155.182.200[7547])
vsys1 222.165.112.234[23]/UNTRUST-L3 (
222.165.112.234[23])
1125 undecided DISCARD FLOW 139.162.91.116[45073]/UNTRUST-L3/
6 (139.162.91.116[45073])
vsys1 222.165.112.234[443]/UNTRUST-L3
(222.165.112.234[443])
1000 web-browsing ACTIVE FLOW NS 172.17.101.3[4395]/TRUST-L3/6 (222.165.112.234[1739])
vsys1 77.234.41.24[80]/UNTRUST-L3 (77.
234.41.24[80])
816 ssl ACTIVE FLOW NS 172.17.101.3[4320]/TRUST-L3/6 (222.165.112.234[47596])
vsys1 124.155.222.163[443]/UNTRUST-L3
(124.155.222.163[443])
696 ssl ACTIVE FLOW NS 172.17.101.3[4283]/TRUST-L3/6 (2
22.165.112.127[10265])
vsys1 104.27.192.92[443]/UNTRUST-L3 (104.27.192.92[443])
800 ssl ACTIVE FLOW NS 172.17.101.3[4315]/TRUST-L3/6 (222.165.112.234[1370])
vsys1 23.50.87.174[443]/UNTRUST-L3 (23.50.87.174[443])
824 ocsp ACTIVE FLOW NS 172.17.101.3[4322]/TRUST-L3/6 (222.165.112.234[6458])
vsys1 23.50.91.27[80]/UNTRUST-L3 (23.5
0.91.27[80])
766 ssl ACTIVE FLOW NS 172.17.101.3[4306]/TRUST-L3/6 (2
22.165.112.127[15483])
vsys1 74.125.200.104[443]/UNTRUST-L3 (74.125.200.104[443])
1128 undecided DISCARD FLOW 134.196.15.164[25680]/UNTRUST-L3/
6 (134.196.15.164[25680])
vsys1 222.165.112.234[5358]/UNTRUST-L3
(222.165.112.234[5358])
856 ssl ACTIVE FLOW NS 172.17.101.3[4335]/TRUST-L3/6 (222.165.112.234[62636])
vsys1 23.50.85.25[443]/UNTRUST-L3 (23.
50.85.25[443])
700 google-talk-base ACTIVE FLOW NS 172.17.101.3[4287]/TRUST-L3/6
(222.165.112.234[26535])
vsys1 74.125.68.188[443]/UNTRUST-L3 (74.125.68.188[443])
177 ssl ACTIVE FLOW NS 172.17.101.3[3549]/TRUST-L3/6 (2
22.165.112.127[19868])
vsys1 172.217.24.98[443]/UNTRUST-L3 (172.217.24.98[443])
912 ssl ACTIVE FLOW NS 172.17.101.3[4356]/TRUST-L3/6 (2
22.165.112.127[20406])
vsys1 23.10.16.154[443]/UNTRUST-L3 (23.10.16.154[443])
You can test NAT policy, Security rule and PBF policy using the test command (similar to Cisco ASA firewall packet-tracer command).
admin@PA-200-LAB> test
> arp ARP related
> botnet Test botnet domain categorization
> cp-policy-match Test cp policy match
> custom-url Test custom URL categorization
> data-filtering Test ccn/ssn match
> decryption-policy-match Test ssl policy match
> dns-proxy Test DNS query
> dos-policy-match Test DoS Policy match
> global-protect-mdm Test MDM
> global-protect-satellite Test GlobalProtect satellite
> nat-policy-match Test nat policy match
> nd IPv6 Neighbor Discovery
> pbf-policy-match Test Policy Based forwarding match
> pppoe test pppoe connection
> qos-policy-match Test qos policy match
> routing verify routing settings
> scp-server-connection Test scp server connection
> security-policy-match Test security policy match
> stats-service Test statistics service
> tag-filter Test a tag-based filter
> url Test URL categorization
> url-info-cloud Return detailed information about the URL in the cloud
--more--
> url-info-host Return detailed information about the URL in the MP
> user-id Test Userid
> vpn verify (IKE/IPSec) VPN settings
> wildfire Test wildfire
admin@PA-200-LAB> test security-policy-match
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ from from
+ protocol IP protocol value
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol
<value> <1-255> IP protocol value
admin@PA-200-LAB> test security-policy-match protocol 1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ from from
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from
TRUST-L3 TRUST-L3
UNTRUST-L3 UNTRUST-L3
any Any
trust trust
untrust untrust
<value> From zone
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
+ to to
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to
TRUST-L3 TRUST-L3
UNTRUST-L3 UNTRUST-L3
any Any
multicast Multicast
trust trust
untrust untrust
<value> To zone
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source source IP address
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source
<ip> <ip>
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1
+ application Application name
+ category Category name
+ destination destination IP address
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination
<ip/netmask> <ip/netmask>
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
+ application Application name
+ category Category name
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8 destination-port
+ application Application name
+ category Category name
+ destination-port Destination port
+ show-all show all potential match rules
+ source-user Source User
| Pipe through a command
<Enter> Finish input
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
<value> <1-65535> Destination port
admin@PA-200-LAB> test security-policy-match protocol 1 from TRUST-L3 to UNTRUST-L3 source 172.17.101.1 destination 8.8.8.8
ALLOW-PING {
from TRUST-L3;
source 172.17.101.0/24;
source-region none;
to UNTRUST-L3;
destination any;
destination-region none;
user any;
category any;
application/service [ ping/any/any/any traceroute/any/any/any ];
action allow;
terminal yes;
}
admin@PA-200-LAB> configure
Entering configuration mode
[edit]
admin@PA-200-LAB# save
> config config
> device-state Save files needed to restore device
admin@PA-200-LAB# save config
+ to Filename
<Enter> Finish input
admin@PA-200-LAB# save config
Config saved to .snapshot.xml















































No comments:
Post a Comment