Security Zones
Palo Alto Networks firewalls are zone based. In order for traffic to pass, the deployment requires that security zones be implemented. These zones act as a logical way to group physical and virtual interfaces. Zones are also required to control and log the traffic that traverses the interfaces. An interface must be of the same type as the zone it is assigned (TAP, Virtual Wire, Layer 2, or Layer 3). In order to pass traffic through an interface, it must be assigned to a zone. A zone can have multiple interfaces of the same type assigned to it, but an interface can belong to only one zone.
All sessions on the firewall are defined by the source and destination zones. Rules can use these defined zones to allow or deny traffic, apply QoS, or perform NAT. All traffic can flow freely within a zone, which is referred to as intrazone traffic. Traffic between zones (interzone traffic) is denied by default. Traffic will be allowed to travel only between zones if a security rule is defined and the rule matches all of the conditions of the session. For interzone traffic, Security policy rules must reference a source zone and destination zone (not interfaces) to allow or deny traffic.
There are three requirements in configuring a Layer 3 interfaces on a PAN firewall:
2) Configure a virtual router (similar to Cisco VRF)
3) Configure interface (bind the security zone, virtual router and IP address)
After the changes were applied, the interface link state turned green (LED lights also turned green).
SW1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface fastethernet0/12
SW1(config-if)#no switchport // TO ENABLE LAYER 3 ON THE SWITCH PORT
SW1(config-if)#
*Mar 1 00:06:11.724: %LINK-3-UPDOWN: Interface FastEthernet0/12, changed state to down
SW1(config-if)#ip address 172.17.99.2 255.255.255.248
SW1(config-if)#no shutdown
SW1(config-if)#end
SW1#
*Mar 1 00:07:38.596: %SYS-5-CONFIG_I: Configured from console by console
SW1#show run interface fastethernet0/12
Building configuration...
Current configuration : 89 bytes
!
interface FastEthernet0/12
no switchport
ip address 172.17.99.2 255.255.255.248
end
*Mar 1 00:37:29.765: %LINK-3-UPDOWN: Interface FastEthernet0/12, changed state to up
*Mar 1 00:37:30.772: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/12, changed state to up // INTERFACE WAS ENABLED AFTER COMMIT WAS EXECUTED
SW1#show interface fastethernet0/12
FastEthernet0/12 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0016.c840.35c1 (bia 0016.c840.35c1)
Internet address is 172.17.99.2/29
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:01:28, output 00:00:05, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 25000 bits/sec, 47 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
20841 packets input, 1333824 bytes, 0 no buffer
Received 20841 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 1 multicast, 0 pause input
0 input packets with dribble condition detected
28 packets output, 2737 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
SW1#ping 172.17.99.1 // UNABLE TO PING PAN FIREWALL IP ADDRESS SINCE ICMP IS BLOCKED BY DEFAULT
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.99.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
SW1#ping 172.17.99.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.99.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/8 ms
I've checked the interface status via CLI since the web GUI only shows Dynamic DHCP Client (under IP Address) and noticed ethernet1/1 didn't receive an auto DHCP public IP address from the ISP.
admin@PA-200-LAB> show interface all
total configured hardware interfaces: 5
name id speed/duplex/state mac address
--------------------------------------------------------------------------------
ethernet1/1 16 100/full/up b4:0c:25:45:58:10
ethernet1/2 17 100/full/up b4:0c:25:45:58:11
vlan 1 [n/a]/[n/a]/up b4:0c:25:45:58:01
loopback 3 [n/a]/[n/a]/up b4:0c:25:45:58:03
tunnel 4 [n/a]/[n/a]/up b4:0c:25:45:58:04
aggregation groups: 0
total configured logical interfaces: 5
name id vsys zone forwarding tag
address
------------------- ----- ---- ---------------- ------------------------ ------
------------------
ethernet1/1 16 1 UNTRUST-L3 vr:LAB-VR 0
N/A
ethernet1/2 17 1 TRUST-L3 vr:LAB-VR 0
172.17.99.1/29
vlan 1 1 N/A 0
N/A
loopback 3 1 N/A 0
N/A
tunnel 4 1 N/A 0
N/A
admin@PA-200-LAB> show interface ethernet1/1
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Link status:
Runtime link speed/duplex/state: 100/full/up
Configured link speed/duplex/state: auto/auto/auto
MAC address:
Port MAC address b4:0c:25:45:58:10
Operation mode: layer3
Untagged sub-interface support: no
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Operation mode: layer3
Virtual router LAB-VR
Interface MTU 1500
Interface IP address (dynamic): 0.0.0.0/0 // NO PUBLIC DHCP IP ADDRESS FROM ISP
Interface management profile: N/A
Service configured:
Zone: UNTRUST-L3, virtual system: vsys1
Adjust TCP MSS: no
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Physical port counters read from MAC:
--------------------------------------------------------------------------------
rx-broadcast 0
rx-bytes 13092710
rx-multicast 0
rx-unicast 204564
tx-broadcast 41
tx-bytes 23766
tx-multicast 2
tx-unicast 78
--------------------------------------------------------------------------------
Hardware interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 12274454
bytes transmitted 24518
packets received 204564
packets transmitted 85
receive errors 0
packets dropped 0
--------------------------------------------------------------------------------
Logical interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 12274454
bytes transmitted 24518
packets received 204564
packets transmitted 85
receive errors 0
packets dropped 0
packets dropped by flow state check 0
forwarding errors 0
no route 0
arp not found 0
neighbor not found 0
neighbor info pending 0
mac not found 0
packets routed to different zone 0
land attacks 0
ping-of-death attacks 0
teardrop attacks 0
ip spoof attacks 0
mac spoof attacks 0
ICMP fragment 0
layer2 encapsulated packets 0
layer2 decapsulated packets 0
--------------------------------------------------------------------------------
admin@PA-200-LAB> ping
+ bypass-routing Bypass routing table, use specified interface
+ count Number of requests to send (1..2000000000 packets)
+ do-not-fragment Don't fragment echo request packets (IPv4)
+ inet6 Force to IPv6 destination
+ interval Delay between requests (seconds)
+ no-resolve Don't attempt to print addresses symbolically
+ pattern Hexadecimal fill pattern
+ size Size of request packets (0..65468 bytes)
+ source Source address of echo request
+ tos IP type-of-service value (0..255)
+ ttl IP time-to-live value (IPv6 hop-limit value) (0..255 hops)
+ verbose Display detailed output
* host Hostname or IP address of remote host
admin@PA-200-LAB> ping source
<value> Source address of echo request
admin@PA-200-LAB> ping source 222.165.123.45
+ bypass-routing Bypass routing table, use specified interface
+ count Number of requests to send (1..2000000000 packets)
+ do-not-fragment Don't fragment echo request packets (IPv4)
+ inet6 Force to IPv6 destination
+ interval Delay between requests (seconds)
+ no-resolve Don't attempt to print addresses symbolically
+ pattern Hexadecimal fill pattern
+ size Size of request packets (0..65468 bytes)
+ tos IP type-of-service value (0..255)
+ ttl IP time-to-live value (IPv6 hop-limit value) (0..255 hops)
+ verbose Display detailed output
* host Hostname or IP address of remote host
admin@PA-200-LAB> ping source 222.165.123.45 host
<value> Hostname or IP address of remote host
admin@PA-200-LAB> ping source 222.165.123.45 host 8.8.8.8
PING 8.8.8.8 (8.8.8.8) from 222.165.123.45 : 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=55 time=8.32 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=55 time=7.16 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=55 time=6.99 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=55 time=8.13 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=55 time=5.76 ms
^C
--- 8.8.8.8 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4032ms
rtt min/avg/max/mdev = 5.763/7.276/8.327/0.924 ms
Palo Alto Networks firewalls are zone based. In order for traffic to pass, the deployment requires that security zones be implemented. These zones act as a logical way to group physical and virtual interfaces. Zones are also required to control and log the traffic that traverses the interfaces. An interface must be of the same type as the zone it is assigned (TAP, Virtual Wire, Layer 2, or Layer 3). In order to pass traffic through an interface, it must be assigned to a zone. A zone can have multiple interfaces of the same type assigned to it, but an interface can belong to only one zone.
All sessions on the firewall are defined by the source and destination zones. Rules can use these defined zones to allow or deny traffic, apply QoS, or perform NAT. All traffic can flow freely within a zone, which is referred to as intrazone traffic. Traffic between zones (interzone traffic) is denied by default. Traffic will be allowed to travel only between zones if a security rule is defined and the rule matches all of the conditions of the session. For interzone traffic, Security policy rules must reference a source zone and destination zone (not interfaces) to allow or deny traffic.
There are three requirements in configuring a Layer 3 interfaces on a PAN firewall:
1) Configure a security zone (similar to Cisco
ZBF)
2) Configure a virtual router (similar to Cisco VRF)
3) Configure interface (bind the security zone, virtual router and IP address)
To configure a zone, go to Network > Zones. There are 2 default zones: trust and untrust which
are both virtual-wire type
(transparent firewall in Cisco ASA)
To add a new zone, click
Add (with the + symbol below) > type the name of the zone > choose the
Type from the drop-down menu (Layer 3 in this case). I’ve created a TRUST-L3 and UNTRUST-L3 which are both Layer 3 interfaces and will allow routing and NAT to function.
The next step is to create a virtual router (similar to Cisco
VRF), which routes traffic between Layer 3 interfaces and allows separate routing tables for different zones and
interfaces. By default, there is a virtual router called default which has no interfaces and
routes added.
Click on More Runtime
Stats on the far right column to view the routing table for each routing
protocol and virtual router created. The default router routing table shows blank since
there’s no interfaces and routes configured yet.
To add a new virtual router, go to Network > Virtual Routers > Add > type a name of the
virtual router (LAB-VR in this case) > click OK.
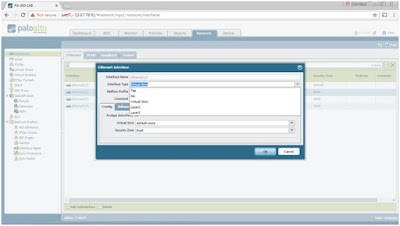
To configure Layer 3 interfaces on a PAN firewall based on the topology, go to Network > Interfaces > click
ethernet1/2 (TRUST-L3).
Choose Layer 3
under Interface Type.
Optionally put a Comment
(LAN Interface in this case) and choose LAB-VR
created earlier under Virtual Router.
Choose TRUST-L3
created earlier under the Security Zone.
Go to IPv4 tab >
choose Static > tick IP > type the IP address/netmask (172.17.99.2/29 in this case) > hit Enter >
click OK.
You can configure IPv6 address under IPv6 tab (not used for this lab).
You can also modify the speed and duplex settings under the Advanced tab. I just leave the default settings to auto.
You configure the UNTRUST-L3 (WAN) interface by clicking on
ethernet1/1.
I’ve configured the IPv4 address to DHCP Client since the ISP (via the cable modem) will automatically
assign a public IP address on the PAN firewall ethernet1/1 interface and
also generate a default route when Automatically
create default route to default gateway provided by server is enabled.
You also need to delete the default-vwire profile under Network
> Virtual Wires since it’s not used for this topology.
To delete default-vwire profile, tick default-vwire > click
Delete (with minus symbol) > choose Yes.
You’ll notice the interfaces configured are still red/down (on the switch port there's no LED light).
To enable these interfaces, you’ll need to click Commit.
After the changes were applied, the interface link state turned green (LED lights also turned green).
SW1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface fastethernet0/12
SW1(config-if)#no switchport // TO ENABLE LAYER 3 ON THE SWITCH PORT
SW1(config-if)#
*Mar 1 00:06:11.724: %LINK-3-UPDOWN: Interface FastEthernet0/12, changed state to down
SW1(config-if)#ip address 172.17.99.2 255.255.255.248
SW1(config-if)#no shutdown
SW1(config-if)#end
SW1#
*Mar 1 00:07:38.596: %SYS-5-CONFIG_I: Configured from console by console
SW1#show run interface fastethernet0/12
Building configuration...
Current configuration : 89 bytes
!
interface FastEthernet0/12
no switchport
ip address 172.17.99.2 255.255.255.248
end
*Mar 1 00:37:29.765: %LINK-3-UPDOWN: Interface FastEthernet0/12, changed state to up
*Mar 1 00:37:30.772: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/12, changed state to up // INTERFACE WAS ENABLED AFTER COMMIT WAS EXECUTED
SW1#show interface fastethernet0/12
FastEthernet0/12 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0016.c840.35c1 (bia 0016.c840.35c1)
Internet address is 172.17.99.2/29
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:01:28, output 00:00:05, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 25000 bits/sec, 47 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
20841 packets input, 1333824 bytes, 0 no buffer
Received 20841 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 1 multicast, 0 pause input
0 input packets with dribble condition detected
28 packets output, 2737 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
I wasn't able to ping the PAN firewall IP address from SW1 since ICMP is blocked by default. To enable ICMP on a PAN firewall, you need to create a Management Profile policy under Network > Network Profiles > Interface Mgmt >
click Add.
SW1#ping 172.17.99.1 // UNABLE TO PING PAN FIREWALL IP ADDRESS SINCE ICMP IS BLOCKED BY DEFAULT
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.99.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Type a name of the Interface Management Profile (MGT-PROF-ICMP in this case) > tick
Ping > then click OK.
To apply the created Interface Mgmt profile, go to Network > Interfaces > click
ethernet1/2 > Advanced tab > choose the Interface Mgmt profile created
MGT-PROF-ICMP > click OK > click Commit.
SW1#ping 172.17.99.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.99.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/8 ms
I've checked the interface status via CLI since the web GUI only shows Dynamic DHCP Client (under IP Address) and noticed ethernet1/1 didn't receive an auto DHCP public IP address from the ISP.
admin@PA-200-LAB> show interface all
total configured hardware interfaces: 5
name id speed/duplex/state mac address
--------------------------------------------------------------------------------
ethernet1/1 16 100/full/up b4:0c:25:45:58:10
ethernet1/2 17 100/full/up b4:0c:25:45:58:11
vlan 1 [n/a]/[n/a]/up b4:0c:25:45:58:01
loopback 3 [n/a]/[n/a]/up b4:0c:25:45:58:03
tunnel 4 [n/a]/[n/a]/up b4:0c:25:45:58:04
aggregation groups: 0
total configured logical interfaces: 5
name id vsys zone forwarding tag
address
------------------- ----- ---- ---------------- ------------------------ ------
------------------
ethernet1/1 16 1 UNTRUST-L3 vr:LAB-VR 0
N/A
ethernet1/2 17 1 TRUST-L3 vr:LAB-VR 0
172.17.99.1/29
vlan 1 1 N/A 0
N/A
loopback 3 1 N/A 0
N/A
tunnel 4 1 N/A 0
N/A
admin@PA-200-LAB> show interface ethernet1/1
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Link status:
Runtime link speed/duplex/state: 100/full/up
Configured link speed/duplex/state: auto/auto/auto
MAC address:
Port MAC address b4:0c:25:45:58:10
Operation mode: layer3
Untagged sub-interface support: no
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Operation mode: layer3
Virtual router LAB-VR
Interface MTU 1500
Interface IP address (dynamic): 0.0.0.0/0 // NO PUBLIC DHCP IP ADDRESS FROM ISP
Interface management profile: N/A
Service configured:
Zone: UNTRUST-L3, virtual system: vsys1
Adjust TCP MSS: no
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Physical port counters read from MAC:
--------------------------------------------------------------------------------
rx-broadcast 0
rx-bytes 13092710
rx-multicast 0
rx-unicast 204564
tx-broadcast 41
tx-bytes 23766
tx-multicast 2
tx-unicast 78
--------------------------------------------------------------------------------
Hardware interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 12274454
bytes transmitted 24518
packets received 204564
packets transmitted 85
receive errors 0
packets dropped 0
--------------------------------------------------------------------------------
Logical interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 12274454
bytes transmitted 24518
packets received 204564
packets transmitted 85
receive errors 0
packets dropped 0
packets dropped by flow state check 0
forwarding errors 0
no route 0
arp not found 0
neighbor not found 0
neighbor info pending 0
mac not found 0
packets routed to different zone 0
land attacks 0
ping-of-death attacks 0
teardrop attacks 0
ip spoof attacks 0
mac spoof attacks 0
ICMP fragment 0
layer2 encapsulated packets 0
layer2 decapsulated packets 0
--------------------------------------------------------------------------------
I tried to bounce ethernet1/1 by going to IPv4 > click Show DHCP Client Runtime Info > click Release > then click Renew. Ethernet1/1 received an ISP public IP address afterwards.
admin@PA-200-LAB> show interface ethernet1/1
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Link status:
Runtime link speed/duplex/state: 100/full/up
Configured link speed/duplex/state: auto/auto/auto
MAC address:
Port MAC address b4:0c:25:45:58:10
Operation mode: layer3
Untagged sub-interface support: no
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Operation mode: layer3
Virtual router LAB-VR
Interface MTU 1500
Interface IP address (dynamic): 222.165.123.45/21 // ISP DHCP PUBLIC IP ADDRESS ASSIGNED
Interface management profile: N/A
Service configured:
Zone: UNTRUST-L3, virtual system: vsys1
Adjust TCP MSS: no
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Physical port counters read from MAC:
--------------------------------------------------------------------------------
rx-broadcast 0
rx-bytes 18118464
rx-multicast 0
rx-unicast 283054
tx-broadcast 56
tx-bytes 29366
tx-multicast 2
tx-unicast 98
--------------------------------------------------------------------------------
Hardware interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 16986248
bytes transmitted 30338
packets received 283054
packets transmitted 106
receive errors 0
packets dropped 0
--------------------------------------------------------------------------------
Logical interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 16986248
bytes transmitted 30338
packets received 283054
packets transmitted 106
receive errors 0
packets dropped 13
packets dropped by flow state check 0
forwarding errors 0
no route 0
arp not found 0
neighbor not found 0
neighbor info pending 0
mac not found 0
packets routed to different zone 0
land attacks 0
ping-of-death attacks 0
teardrop attacks 0
ip spoof attacks 0
mac spoof attacks 0
ICMP fragment 0
layer2 encapsulated packets 0
layer2 decapsulated packets 0
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Link status:
Runtime link speed/duplex/state: 100/full/up
Configured link speed/duplex/state: auto/auto/auto
MAC address:
Port MAC address b4:0c:25:45:58:10
Operation mode: layer3
Untagged sub-interface support: no
--------------------------------------------------------------------------------
Name: ethernet1/1, ID: 16
Operation mode: layer3
Virtual router LAB-VR
Interface MTU 1500
Interface IP address (dynamic): 222.165.123.45/21 // ISP DHCP PUBLIC IP ADDRESS ASSIGNED
Interface management profile: N/A
Service configured:
Zone: UNTRUST-L3, virtual system: vsys1
Adjust TCP MSS: no
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Physical port counters read from MAC:
--------------------------------------------------------------------------------
rx-broadcast 0
rx-bytes 18118464
rx-multicast 0
rx-unicast 283054
tx-broadcast 56
tx-bytes 29366
tx-multicast 2
tx-unicast 98
--------------------------------------------------------------------------------
Hardware interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 16986248
bytes transmitted 30338
packets received 283054
packets transmitted 106
receive errors 0
packets dropped 0
--------------------------------------------------------------------------------
Logical interface counters read from CPU:
--------------------------------------------------------------------------------
bytes received 16986248
bytes transmitted 30338
packets received 283054
packets transmitted 106
receive errors 0
packets dropped 13
packets dropped by flow state check 0
forwarding errors 0
no route 0
arp not found 0
neighbor not found 0
neighbor info pending 0
mac not found 0
packets routed to different zone 0
land attacks 0
ping-of-death attacks 0
teardrop attacks 0
ip spoof attacks 0
mac spoof attacks 0
ICMP fragment 0
layer2 encapsulated packets 0
layer2 decapsulated packets 0
--------------------------------------------------------------------------------
admin@PA-200-LAB> ping
+ bypass-routing Bypass routing table, use specified interface
+ count Number of requests to send (1..2000000000 packets)
+ do-not-fragment Don't fragment echo request packets (IPv4)
+ inet6 Force to IPv6 destination
+ interval Delay between requests (seconds)
+ no-resolve Don't attempt to print addresses symbolically
+ pattern Hexadecimal fill pattern
+ size Size of request packets (0..65468 bytes)
+ source Source address of echo request
+ tos IP type-of-service value (0..255)
+ ttl IP time-to-live value (IPv6 hop-limit value) (0..255 hops)
+ verbose Display detailed output
* host Hostname or IP address of remote host
admin@PA-200-LAB> ping source
<value> Source address of echo request
admin@PA-200-LAB> ping source 222.165.123.45
+ bypass-routing Bypass routing table, use specified interface
+ count Number of requests to send (1..2000000000 packets)
+ do-not-fragment Don't fragment echo request packets (IPv4)
+ inet6 Force to IPv6 destination
+ interval Delay between requests (seconds)
+ no-resolve Don't attempt to print addresses symbolically
+ pattern Hexadecimal fill pattern
+ size Size of request packets (0..65468 bytes)
+ tos IP type-of-service value (0..255)
+ ttl IP time-to-live value (IPv6 hop-limit value) (0..255 hops)
+ verbose Display detailed output
* host Hostname or IP address of remote host
admin@PA-200-LAB> ping source 222.165.123.45 host
<value> Hostname or IP address of remote host
admin@PA-200-LAB> ping source 222.165.123.45 host 8.8.8.8
PING 8.8.8.8 (8.8.8.8) from 222.165.123.45 : 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=55 time=8.32 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=55 time=7.16 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=55 time=6.99 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=55 time=8.13 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=55 time=5.76 ms
^C
--- 8.8.8.8 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4032ms
rtt min/avg/max/mdev = 5.763/7.276/8.327/0.924 ms