Tunnel Interfaces
Tunnel interfaces specifically serve VPN tunnels and are Layer 3 only.
To set up a VPN tunnel, you must configure the Layer 3 interface at each end
and have a logical tunnel interface for the firewall to connect to and
establish a VPN tunnel. A tunnel interface is a logical (virtual) interface
that is used to deliver traffic between two endpoints. Each tunnel interface
can have a maximum of 10 IPSec tunnels, which means that up to 10 networks can
be associated with the same tunnel interface on the firewall.
The tunnel interface must belong to a security zone to apply policy and
it must be assigned to a virtual router in order to use the existing routing
infrastructure. Ensure that the tunnel interface and the physical interface are
assigned to the same virtual router so that the firewall can perform a route
lookup and determine the appropriate tunnel to use.
Typically, the Layer 3 interface that the tunnel interface is attached
to belongs to an external zone, for example, the untrust zone. Although the tunnel
interface can be in the same security zone as the physical interface, for added
security and better visibility you can create a separate zone for the tunnel
interface. If you create a separate zone for the tunnel interface (for example,
a VPN zone), you will need to create Security policies to enable traffic to
flow between the VPN zone and the trust zone.
A tunnel interface does not require an IP address to route traffic
between the sites. An IP address is required only if you want to enable tunnel monitoring
or if you are using a dynamic routing protocol to route traffic across the
tunnel. With dynamic routing, the tunnel IP address serves as the next-hop IP
address for routing traffic to the VPN tunnel.
The detailed site-to-site IPSec VPN configuration can be found on this link.
I've configured a Cisco 2811 router with a Security K9 IOS for the
remote IPSec VPN peer. You'll need to configure the IKE Phase 1 and Phase 2
(IPSec) security policies and apply it (using crypto map profile) on the WAN
interface. An identical IKE Phase 1 and Phase 2 policies needs to be configured
on the PAN firewall.
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface fastethernet0/0
R1(config-if)#interface loopback1 //
INTERFACE TO SIMULATE THE LAN INTERFACE
R1(config-if)#
*Mar 15 11:39:21.859: %LINEPROTO-5-UPDOWN: Line protocol on Interface
Loopback1, changed state to up
R1(config-if)#ip address 172.18.101.1
255.255.255.0 // REMOTE SITE
LAN IP ADDRESS
R1(config-if)#exit
R1(config)#crypto isakmp ?
aggressive-mode Disable
ISAKMP aggressive mode
client
Set client configuration policy
default
ISAKMP default policy
enable
Enable ISAKMP
fragmentation IKE
Fragmentation enabled if required
identity
Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI
Notify
keepalive
Set a keepalive interval for use with IOS peers
key
Set pre-shared key for remote peer
nat
Set a nat keepalive interval for use with IOS peers
peer
Set Peer Policy
policy
Set policy for an ISAKMP protection suite
profile
Define ISAKMP Profiles
xauth
Set Extended Authentication values
R1(config)#crypto isakmp policy ?
<1-10000> Priority of protection suite
R1(config)#crypto isakmp policy 10
// IKE PHASE 1 POLICY
R1(config-isakmp)#?
ISAKMP commands:
authentication Set authentication method for protection
suite
default Set a
command to its defaults
encryption Set encryption algorithm
for protection suite
exit Exit
from ISAKMP protection suite configuration mode
group
Set the Diffie-Hellman group
hash Set hash
algorithm for protection suite
lifetime Set lifetime
for ISAKMP security association
no
Negate a command or set its defaults
R1(config-isakmp)#encryption ?
3des Three key triple DES
aes AES - Advanced Encryption Standard.
des DES - Data Encryption Standard (56 bit keys).
R1(config-isakmp)#encryption aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
<cr>
R1(config-isakmp)#encryption aes 128
R1(config-isakmp)#hash ?
md5 Message Digest 5
sha Secure Hash Standard
sha256 Secure Hash Standard 2 (256 bit)
sha384 Secure Hash Standard 2 (384 bit)
sha512 Secure Hash Standard 2 (512 bit)
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication ?
pre-share Pre-Shared Key
rsa-encr Rivest-Shamir-Adleman Encryption
rsa-sig Rivest-Shamir-Adleman Signature
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group ?
1 Diffie-Hellman group 1 (768 bit)
14 Diffie-Hellman group 14 (2048 bit)
15 Diffie-Hellman group 15 (3072 bit)
16 Diffie-Hellman group 16 (4096 bit)
19 Diffie-Hellman group 19 (256 bit ecp)
2 Diffie-Hellman group 2 (1024 bit)
20 Diffie-Hellman group 20 (384 bit ecp)
24 Diffie-Hellman group 24 (2048 bit, 256 bit subgroup)
5 Diffie-Hellman group 5 (1536 bit)
R1(config-isakmp)#group 2
R1(config-isakmp)#lifetime ?
<60-86400> lifetime in seconds
R1(config-isakmp)#lifetime 28800
R1(config-isakmp)#exit
R1(config)#crypto isakmp ?
aggressive-mode Disable
ISAKMP aggressive mode
client
Set client configuration policy
default
ISAKMP default policy
enable
Enable ISAKMP
fragmentation IKE
Fragmentation enabled if required
identity
Set the identity which ISAKMP will use
invalid-spi-recovery Initiate IKE and send Invalid SPI
Notify
keepalive
Set a keepalive interval for use with IOS peers
key
Set pre-shared key for remote peer
nat
Set a nat keepalive interval for use with IOS peers
peer
Set Peer Policy
policy
Set policy for an ISAKMP protection suite
profile
Define ISAKMP Profiles
xauth
Set Extended Authentication values
R1(config)#crypto isakmp key ?
0 Specifies an UNENCRYPTED password will
follow
6 Specifies an ENCRYPTED password will
follow
WORD The UNENCRYPTED (cleartext) user password
R1(config)#crypto isakmp key cisco123 ?
address define shared key with IP address
hostname define shared key with hostname
R1(config)#crypto isakmp key cisco123 address ?
A.B.C.D Peer IP address
ipv6 define shared key with IPv6 address
R1(config)#crypto isakmp key cisco123 address
108.81.248.145 // CONFIGURE THE SAME PRE-SHARED
KEY ON THE PAN FIREWALL
R1(config)#crypto ipsec ?
client
Configure a client
default
Default transform-set
df-bit
Handling of encapsulated DF bit.
fragmentation
Handling of fragmentation of near-MTU sized packets
nat-transparency IPsec NAT transparency
model
optional
Enable optional encryption for IPSec
profile
Configure an ipsec policy profile
security-association Security association parameters
transform-set
Define transform and settings
R1(config)#crypto ipsec transform-set ?
WORD Transform set tag
R1(config)#crypto ipsec transform-set TSET ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
ah-sha256-hmac AH-HMAC-SHA256 transform
ah-sha384-hmac AH-HMAC-SHA384 transform
ah-sha512-hmac AH-HMAC-SHA512 transform
comp-lzs IP
Compression using the LZS compression algorithm
esp-3des ESP
transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP
transform using AES cipher
esp-des ESP
transform using DES cipher (56 bits)
esp-gcm ESP
transform using GCM cipher
esp-gmac ESP
transform using GMAC cipher
esp-md5-hmac ESP transform using HMAC-MD5
auth
esp-null ESP
transform w/o cipher
esp-seal ESP
transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA
auth
esp-sha256-hmac ESP transform using HMAC-SHA256 auth
esp-sha384-hmac ESP transform using HMAC-SHA384 auth
esp-sha512-hmac ESP transform using HMAC-SHA512 auth
R1(config)#crypto ipsec transform-set TSET esp-aes ?
128
128 bit keys.
192
192 bit keys.
256
256 bit keys.
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
ah-sha256-hmac AH-HMAC-SHA256 transform
ah-sha384-hmac AH-HMAC-SHA384 transform
ah-sha512-hmac AH-HMAC-SHA512 transform
comp-lzs IP
Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5
auth
esp-sha-hmac ESP transform using HMAC-SHA
auth
esp-sha256-hmac ESP transform using HMAC-SHA256 auth
esp-sha384-hmac ESP transform using HMAC-SHA384 auth
esp-sha512-hmac ESP transform using HMAC-SHA512 auth
<cr>
R1(config)#crypto ipsec transform-set TSET esp-aes 128 ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
ah-sha256-hmac AH-HMAC-SHA256 transform
ah-sha384-hmac AH-HMAC-SHA384 transform
ah-sha512-hmac AH-HMAC-SHA512 transform
comp-lzs IP
Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5
auth
esp-sha-hmac ESP transform using HMAC-SHA
auth
esp-sha256-hmac ESP transform using HMAC-SHA256 auth
esp-sha384-hmac ESP transform using HMAC-SHA384 auth
esp-sha512-hmac ESP transform using HMAC-SHA512 auth
<cr>
R1(config)#crypto ipsec transform-set TSET esp-aes 128
esp-sha-hmac // IKE PHASE 2 (IPSEC) POLICY
R1(cfg-crypto-trans)#exit
R1(config)#ip access-list extended S2S-VPN-ACL
R1(config-ext-nacl)#permit ip 172.18.0.0 0.0.255.255 172.17.0.0
0.0.255.255 // MIRROR THE CRYPTO ACL IN PAN FIREWALL PROXY-ID IKE GATEWAY PROFILE
R1(config-ext-nacl)#exit
R1(config)#crypto map ?
WORD Crypto map tag
ipv6 IPv6 crypto map
R1(config)#crypto map CMAP ?
<1-65535> Sequence to
insert into crypto map entry
client
Specify client configuration settings
gdoi
Configure crypto map gdoi features
isakmp Specify
isakmp configuration settings
isakmp-profile Specify isakmp profile to use
local-address Interface to use for local address for
this crypto map
redundancy High availability
options for this map
R1(config)#crypto map CMAP 10 ?
gdoi GDOI
ipsec-isakmp IPSEC w/ISAKMP
ipsec-manual IPSEC w/manual keying
<cr>
R1(config)#crypto map CMAP 10 ipsec-isakmp
// APPLY CRYPTO MAP ON R1 WAN INTERFACE (F0/0)
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have
been configured.
R1(config-crypto-map)#?
Crypto Map configuration commands:
default Set a command
to its defaults
description Description of the crypto map
statement policy
dialer Dialer
related commands
exit
Exit from crypto map configuration mode
match Match
values.
no
Negate a command or set its defaults
qos Quality
of Service related commands
reverse-route Reverse Route Injection.
set
Set values for encryption/decryption
R1(config-crypto-map)#set ?
identity
Identity restriction.
ikev2-profile
Specify ikev2 Profile
ip
Interface Internet Protocol config commands
isakmp-profile Specify
isakmp Profile
nat
Set NAT translation
peer
Allowed Encryption/Decryption peer.
pfs
Specify pfs settings
reverse-route
Reverse Route Injection.
security-association Security association parameters
transform-set
Specify list of transform sets in priority order
R1(config-crypto-map)#set peer 108.81.248.145
R1(config-crypto-map)#set transform-set TSET
R1(config-crypto-map)#set pfs ?
group1 D-H Group1 (768-bit modp)
group14 D-H Group14 (2048-bit modp)
group15 D-H Group15 (3072-bit modp)
group16 D-H Group16 (4096-bit modp)
group19 D-H Group19 (256-bit ecp)
group2 D-H Group2 (1024-bit modp)
group20 D-H Group20 (384-bit ecp)
group24 D-H Group24 (2048-bit modp, 256 bit subgroup)
group5 D-H Group5 (1536-bit modp)
<cr>
R1(config-crypto-map)#set
pfs group2 // DEFAULT DH GROUP IN PAN FIREWALL IPSEC CRYPTO PROFILE
R1(config-crypto-map)#match ?
address Match address of packets to encrypt.
R1(config-crypto-map)#match address ?
<100-199> IP access-list number
<2000-2699> IP access-list number (expanded range)
WORD Access-list
name
R1(config-crypto-map)#match address S2S-VPN-ACL
R1(config-crypto-map)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 ?
A.B.C.D
Forwarding router's address
Async
Async interface
Auto-Template Auto-Template
interface
BVI
Bridge-Group Virtual Interface
CDMA-Ix
CDMA Ix interface
CTunnel
CTunnel interface
DHCP
Default Gateway obtained from DHCP
Dialer
Dialer interface
FastEthernet
FastEthernet IEEE 802.3
LISP
Locator/ID Separation Protocol Virtual Interface
Lex
Lex interface
LongReachEthernet Long-Reach Ethernet interface
Loopback
Loopback interface
MFR
Multilink Frame Relay bundle interface
Multilink
Multilink-group interface
Null
Null interface
Port-channel Ethernet
Channel of interfaces
Tunnel
Tunnel interface
Vif
PGM Multicast Host interface
Virtual-Dot11Radio Virtual dot11 interface
Virtual-PPP
Virtual PPP interface
Virtual-TokenRing Virtual TokenRing
vmi
Virtual Multipoint Interface
R1(config)#ip
route 0.0.0.0 0.0.0.0 fastethernet0/0 // USING
NEXT-HOP AS EXIT INTERFACE IS NOT ADVISABLE IN A PRODUCTION NETWORK
%Default
route without gateway, if not a point-to-point interface, may impact
performance
R1(config)#interface fastethernet0/0
R1(config-if)#crypto ?
ipsec Set IPSec parameters
map Assign a Crypto Map
R1(config-if)#crypto map ?
WORD Crypto Map tag
R1(config-if)#crypto map CMAP
R1(config-if)#
*Mar 15 11:43:13.119: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1#show ip interface brief
Interface
IP-Address OK? Method
Status
Protocol
FastEthernet0/0
108.81.248.146 YES manual
up
up
FastEthernet0/1
unassigned YES manual
up
down
Loopback1
172.18.101.1 YES manual
up
up
NVI0
unassigned YES unset administratively down
down
R1#show run
Building configuration...
Current configuration : 1491 bytes
!
! Last configuration change at 11:44:49 UTC Wed Mar 15 2017
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
enable password cisco
!
no aaa new-model
!
!
dot11 syslog
ip source-route
!
!
ip cef
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
crypto pki token default removal timeout 0
!
!
!
!
license udi pid CISCO2811 sn FHK1308F18L
!
redundancy
!
!
!
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
lifetime 28800
crypto isakmp key cisco123 address 108.81.248.145
!
!
crypto ipsec transform-set TSET esp-aes esp-sha-hmac
!
crypto map CMAP 10 ipsec-isakmp
set peer 108.81.248.145
set transform-set TSET
set pfs group2
match address S2S-VPN-ACL
!
!
!
!
!
interface Loopback1
ip address 172.18.101.1 255.255.255.0
!
interface FastEthernet0/0
ip address 108.81.248.146 255.255.255.248
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
crypto map CMAP
!
interface FastEthernet0/1
no ip address
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
ip access-list extended S2S-VPN-ACL
permit ip 172.18.0.0 0.0.255.255 172.17.0.0 0.0.255.255
!
!
!
!
!
!
control-plane
!
!
banner motd ^C
*** R1 ***
^C
!
line con 0
line aux 0
line vty 0 4
password cisco
login
transport input all
!
scheduler allocate 20000 1000
end
The site-to-site IPSec VPN tunnel hasn't established since the PAN
firewall isn't configured yet. I ran some debugs on the router to monitor
handshake of the Security Association (SA) between the two VPN peers.
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst
src
state conn-id status
IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CMAP, local addr 108.81.248.146
protected vrf: (none)
local ident (addr/mask/prot/port):
(172.18.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port):
(172.17.0.0/255.255.0.0/0/0)
current_peer 108.81.248.145 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 108.81.248.146, remote
crypto endpt.: 108.81.248.145
path mtu 1500, ip mtu 1500, ip mtu idb
FastEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R1#debug crypto ?
ber
decode ASN.1 BER data
condition Define debug condition filters
ctcp cTCP
debugging
engine Crypto Engine
Debug
gdoi Crypto
GDOI Group Key Management debug
ha Crypto
High Availability (generic) debug
ipsec IPSEC
processing
ipv6 Crypto
IPv6 debug
isakmp ISAKMP Key
Management
kmi
Crypto Key Management Interface debug
mib
IPSEC Management Transactions
pki
PKI Client
provisioning Crypto provisioning configuration
rmal Crypto
RMAL debug
routing IPSEC Route Events
socket Crypto Secure
Socket Debug
verbose verbose decode
R1#debug crypto isakmp ?
aaa ISAKMP AAA
error ISAKMP Errors
ha ISAKMP High Availability
<cr>
R1#debug crypto isakmp
Crypto ISAKMP debugging is on
R1#debug crypto ipsec ?
client Client Debug
error IPSEC errors
ha IPSEC High Availability
<cr>
R1#debug crypto ipsec
Crypto IPSEC debugging is on
I’ve configured the PAN firewall WAN interface (UNTRUST-L3) with a
public IP address of 108.81.248.145/28.
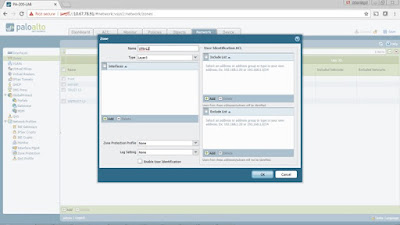
Create a custom Layer 3 zone for the VPN tunnel interface by going
to Network > Zone> Add.
Type the zone name (in this case VPN-L3) > leave all fields in
default > click OK.
Configure a tunnel interface to terminate the site-to-site VPN traffic
between the PAN firewall and VPN peer R1 by going to Network >
Interfaces > Tunnel > Add.
You can’t change the tunnel Interface Name > type (in this case 1)
the tunnel sub-interface (you can choose from 1-9999) > optionally add a
Comment > choose LAB-VR under Virtual Router > choose VPN-L3 under
Security Zone > click OK.
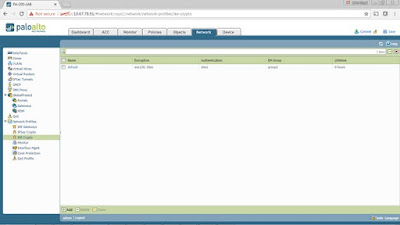
Create the IKE Phase 1 policies by going to Network > Network
Profiles > IKE Crypto > Add.
Type a Name for the IKE Crypto Profile (IKE-P1-PROF-1) > choose group
2 under DH Group > choose sha1 under Authentication > choose aes128 under
Encryption > choose Seconds under Lifetime > type 28800 (seconds).
Create an IPSec (IKE Phase 2) Policy by going to Network >
Network Profiles > Add.
Type the IPSec Crypto Profile Name (IPSEC-P2-PROF-1) > choose ESP
(which is a common and more secure protocol) under IPSec Protocol > choose
aes128 under Encryption > choose sha1 under Authentication > leave the
default group2 under DH Group (PFS under router crypto map config) > leave
the default of 1 Hour under Lifetime (the lower lifetime is always negotiated
on the IPSec VPN Security Association) > click OK.
Configure an IKE Gateway that will peer or handshake with R1 by going to Network > Network Profiles > IKE Gateway > Add.
Type a Name of the IKE Gateway (IKE-GW-1) > choose ethernet1/1
(UNTRUST-L3) under Interface > choose the IP address 108.81.248.145/28 under
Local IP Address > leave the default of Static under Peer IP Type > type
108.81.248.146/28 (the public WAN IP address on R1) under Peer IP Address >
leave the default Pre Shared Key under Authentication > type the Pre-Shared
Key twice (cisco123) which should be the same on R1 > click OK.
Create an IPSec tunnel to bind the IKE Gateway and IPSec Crypto profile
that was created earlier by going to Network > IPSec Tunnels >
Add.
Type a Name for the IPSec Tunnel (IPSEC-TUNNEL-1) > choose tunnel.1
under Tunnel Interface > leave the default of Auto Key under Type >
choose the IKE Gateway created (IKE-GW-1) > choose
the IPSec Crypto Profile (IPSEC-P2-PROF-1).
To configure the mirrored crypto ACL (reverse crypto ACL on R1) on the
PAN firewall go to Proxy IDs tab > click Add.
Type a Proxy ID name (S2S-VPN-ACL) > type 172.17.0.0/16 under Local
(the TRUST-L3 network) > type 172.18.0.0/16 (which is the LAN behind R1)
> leave the default of Any under Protocol > click OK.
You'll notice the Status of the IPSec Tunnel is red (down) since there's
no static route to 172.18.0.0/16 and we haven't clicked Commit yet.
To configure a static route for the remote site VPN go to Network
> Virtual Routers > click LAB-VR.
Go to Static Routes > IPv4 > click Add.
Type a Name (R1-REMOTE-LAN) for the static route > type 172.18.0.0/16 under Destination > choose tunnel.1 under Interface > choose None under Next Hop > click OK.
The final step is to configure a Security rule that will allow the
site-to-site (LAN-to-LAN) IPSec VPN traffic between the PAN firewall and R1.
You go to Policies > Security > Add.
Type a Name for the Security rule (S2S-VPN-R1) > optionally type a
Description.
Under Source tab > add TRUST-L3 and VPN-L3 zones under Source Zone > leave the default of Any under Source Address.
Under Destinations tab > add TRUST-L3 and VPN-L3 zones > leave the default of Any under Destination Address.
You can check the Status of the IPSec Tunnel is still down (red) under Network > IPSec Tunnels. You need to generate an "interesting" network traffic to trigger and establish the IPSec VPN tunnel. I tried pinging from a user PC (172.17.101.50) on the TRUST-L3 zone to R1 LAN IP address (172.18.101.1).
H:\>ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . : rignet.org
IPv4 Address. . . . . . . . . . . : 172.17.101.50
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.17.101.1
H:\>ping 172.17.101.1 // PING TO SW1 SVI GATEWAY IP
Pinging 172.17.101.1 with 32 bytes of data:
Reply from 172.17.101.1: bytes=32 time=2ms TTL=255
Reply from 172.17.101.1: bytes=32 time=2ms TTL=255
Reply from 172.17.101.1: bytes=32 time=5ms TTL=255
Reply from 172.17.101.1: bytes=32 time=1ms TTL=255
Ping statistics for 172.17.101.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 5ms, Average = 2ms
H:\>ping 172.18.101.1 // PING TO R1 LAN GATEWAY IP
Pinging 172.18.101.1 with 32 bytes of data:
Reply from 172.18.101.1: bytes=32 time=3ms TTL=253
Reply from 172.18.101.1: bytes=32 time=3ms TTL=253
Reply from 172.18.101.1: bytes=32 time=3ms TTL=253
Reply from 172.18.101.1: bytes=32 time=3ms TTL=253
Ping statistics for 172.18.101.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 3ms, Maximum = 3ms, Average = 3ms
H:\>tracert 172.18.101.1
Tracing route to 172.18.101.1 over a maximum of 30 hops
1 2 ms 1 ms 1 ms 172.17.101.1
2 1 ms <1 ms <1 ms 172.17.99.1
3 3 ms 3 ms 3 ms 172.18.101.1
Trace complete.
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
108.81.248.146 108.81.248.145 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
The Status of the IPSec Tunnel went up or turned green.
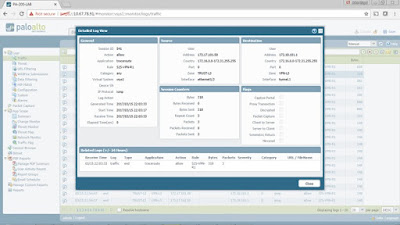
To view successful IPSec VPN traffic flows, go to Monitor > App Scope > Session Browser. You can expand to view more details by clicking the plus (+) icon.
The IPSec Tunnel remained down and didn't automatically re-established itself even when I was doing a continuous ping from the PC on the TRUST-L3 zone to R1's LAN IP address. You also need to clear the SA on the PAN firewall via the CLI. In PAN 7.0, there's an option to Refresh/Restart both the IKE Gateway (IKE Phase 1) and IPSec Tunnel (IKE Phase 2) via the web GUI.
admin@PA-200-LAB> clear vpn ike-sa
+ gateway clear for given IKE gateway
<Enter> Finish input
admin@PA-200-LAB> clear vpn ike-sa gateway
IKE-GW-1 IKE-GW-1
<value> clear for given IKE gateway
admin@PA-200-LAB> clear vpn ike-sa gateway IKE-GW-1
Delete IKEv1 IKE SA: Total 1 gateways found. 1 ike sa found.
admin@PA-200-LAB> clear vpn ipsec-sa
+ tunnel clear for given VPN tunnel
<Enter> Finish input
admin@PA-200-LAB> clear vpn ipsec-sa tunnel
IPSEC-TUNNEL-1 IPSEC-TUNNEL-1
<value> clear for given VPN tunnel
admin@PA-200-LAB> clear vpn ipsec-sa tunnel IPSEC-TUNNEL-1
Delete IKEv1 IPSec SA: Total 1 tunnels found. 1 ipsec sa found.
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
108.81.248.146 108.81.248.145 QM_IDLE 1003 ACTIVE // IT GENERATED A NEW CONNECTION-ID (INITIALLY WAS 1001)
IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CMAP, local addr 108.81.248.146
protected vrf: (none)
local ident (addr/mask/prot/port): (172.18.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (172.17.0.0/255.255.0.0/0/0)
current_peer 108.81.248.145 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 108.81.248.146, remote crypto endpt.: 108.81.248.145
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x92BB4A5C(2461747804)
PFS (Y/N): Y, DH group: group2
inbound esp sas:
spi: 0xE3D547B7(3822405559)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: NETGX:5, sibling_flags 80000046, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4382614/3303)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
spi: 0x53229582(1394775426)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2007, flow_id: NETGX:7, sibling_flags 80000046, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4483493/3404)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xEC0F270E(3960416014)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: NETGX:6, sibling_flags 80000046, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4382614/3303)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
spi: 0x92BB4A5C(2461747804)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2008, flow_id: NETGX:8, sibling_flags 80000046, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4483493/3404)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
The Status of the IPSec Tunnel was re-established and went up again.



























































No comments:
Post a Comment